Understanding Your Attack Surface

What is an Attack Surface?
An attack surface refers to all the assets through which an adversary could potentially compromise your organization’s security. Assets span from technical infrastructure to applications to people. Crucially, how an attacker views your attack surface often differs from how your internal IT and security teams perceive it.
Attackers take an external, offense-oriented perspective. They don’t care about your network diagrams, asset inventories, or organizational boundaries. If they can reach an asset from the outside and exploit it to gain entry, it’s part of your attack surface - even if you’ve never cataloged that asset internally. “Shadow IT”, forgotten servers, dangling DNS records, and assets spun up outside normal processes all expand your real attack surface beyond what most IT inventories capture.
Meanwhile, internal teams focus on maintaining uptime, availability, and performance for business-critical assets. Security is important but balanced against other priorities. Gaps emerge because no single team has a complete picture of what the corporate assets look like externally. As attackers, we always find bugs where there’s “glue” - where the pieces of software or networks are joined together.
Take the Adversary’s Perspective
To manage risk, organizations must view their attack surface through an adversary’s lens. We can break it down into three main areas:
- People, whom attackers target via social engineering
- Applications, which introduce risks via vulnerabilities and misconfigurations
- Networks and infrastructure, the traditional attack surface of exposed IPs/ports/services
In modern networks and companies, the attack surface constantly changes. New vulnerabilities emerge daily. Acquisitions and cloud adoption create complexity. Development teams spin up infrastructure far faster than asset inventories can be updated. “Defending forward” requires frequently re-evaluating your attack surface from the outside-in, not just once or twice per year.
The Attack Surface Series
In this blog series, we’ll dive deeper into how attackers target each area of the attack surface and the keys to managing these risks proactively. By understanding your organization the way an attacker does, you can focus defenses where they matter the most.
We will cover the following attack surfaces in this series (and we’ll link them as they’re published):
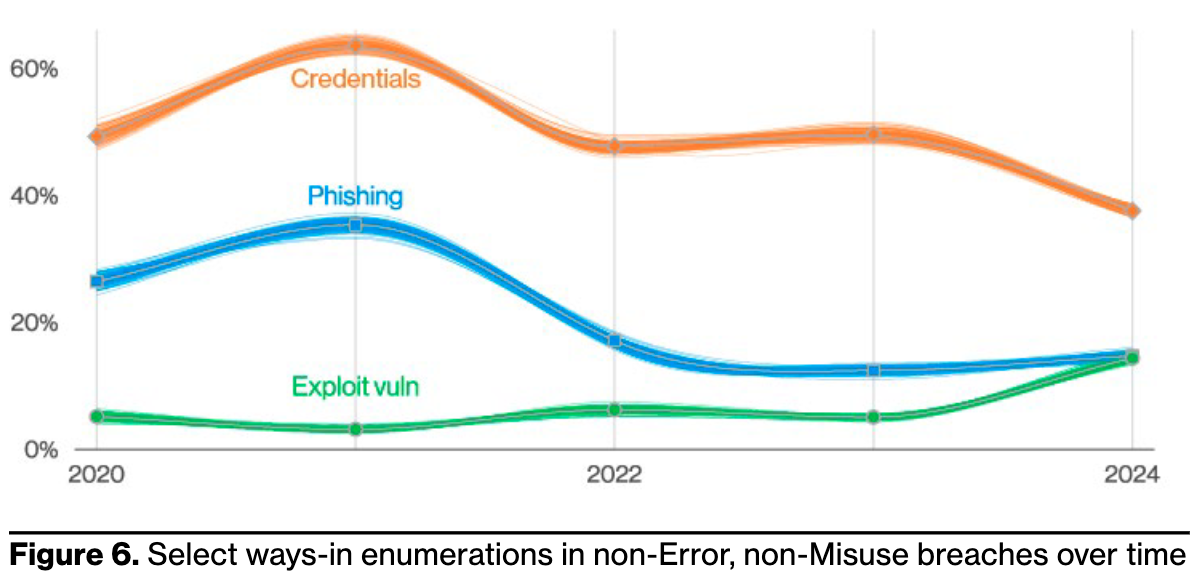
Why these three? Because the data show that these are the most common ways attackers compromise organizations. The 2024 Verizon Data Breach Investigations Report (DBIR) shows us the relative importance of these attack surfaces based on real adversary actions. In the diagram below, Credentials and Exploit vuln target your Applications and Networks/Infrastructure attack surfaces. Phishing (and arguably Credentials here as well) targets your People attack surface. All 3 comprise a significant portion of breaches, and shift year to year based on the path of least resistance for attackers. Excerpted from the 2024 DBIR report: