WASM Security Assessment Techniques

Do we have a problem?
The World Wide Web have been struggling with how to create portable, efficient and safe programs (pick two) for decades. The current best of breed attempt is called WebAssembly and is affectionately referred to as “WASM”. The project defines WASM broadly as:
WebAssembly (abbreviated Wasm) is a binary instruction format for a stack-based virtual machine. Wasm is designed as a portable compilation target for programming languages, enabling deployment on the web for client and server applications.
From a security perspective, there has been some focus on discovering exploits in WASM runtime implementations and programs. This is extremely interesting work that shows the outcome of vulnerability research. However, how would someone go about finding vulnerabilities themselves?
We will only focus on analyzing WASM programs and not runtime implementations. With that in mind, there are two tools/techniques that will be of great help — (1) Reverse Engineering and (2) Web Proxying.
Reverse Engineering
WASM has a text format that can be used as a target to disassemble binary WASM programs. All modern browsers provide a way to disassemble programs to the text format. Furthermore, there are tools like the WebAssembly Binary Toolkit that provide several programs for producing a text format. These programs are not sufficient for serious reverse engineering work.
Why not? For start, they are not interactive. You can’t annotate the code with notes, rename functions and variables, or get a graphical view of the program. Second, these systems do not allow for effective programmatic analysis — the ability to write computer programs that can analyze and/or mutate WASM programs.
To help with this problem I have released a Python library for analyzing WASM programs named wasamole. Wasamole has been used to create a Binary Ninja plugin called Binjawa which will help make reverse engineering easier.
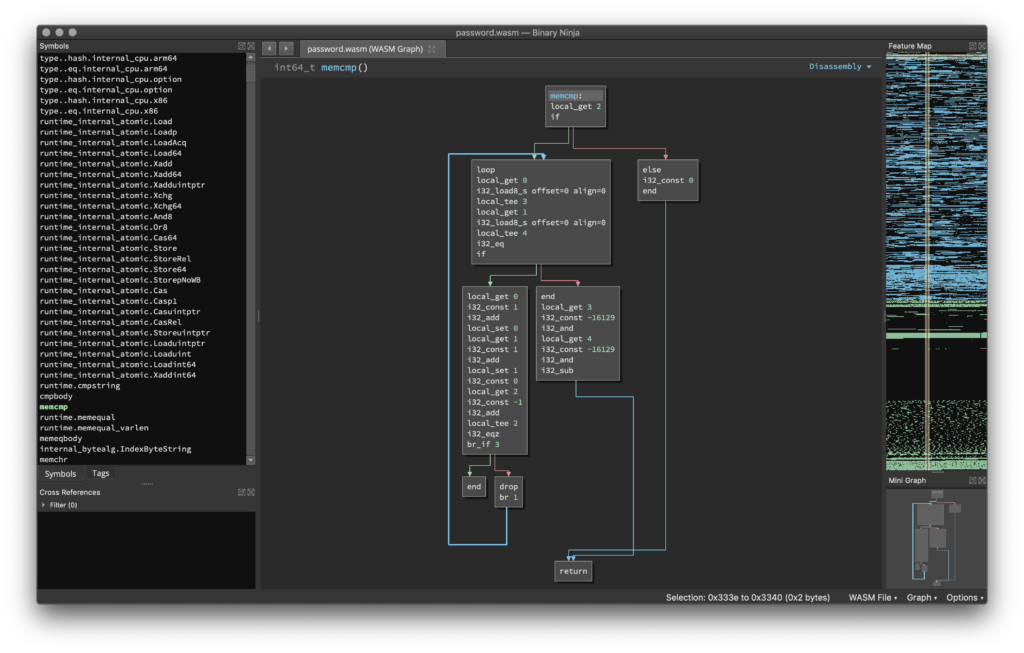
Web Proxying
Given that one of the main applications of WASM is programs running in the browser, it is only natural that web proxies such as Burp and mitmproxy will be used. Neither Burp or mitmproxy (at the time of writing) have support for decoding WASM. To help with this, I have written a mitmproxy plugin based on wasamole to decode WASM.

Conclusion
Reverse engineering and proxying are only two tools/techniques in a security engineer’s toolbox, but they are very powerful. Wasamole and Binjawa provide a great foundation for creating tools in this space. We have already found them useful and look forward to growing their functionality.
Patches welcome!
